Introduction Financial institutions are under attack by all manner of cyber thieves. And why not? As Willie Sutton...
PCI Compliance: How to Develop a Remediation Plan
By Jane Laroussi, CISSP, QSA This is the fifth of a six-part blog series about PCI compliance. In recent weeks, we...
Measuring Success in Cybersecurity
At Carson Inc., we understand how to develop enterprise risk management architectures, identify vulnerabilities, establish continuous monitoring programs, assess organizational exposure, and implement appropriate preventive measures. It is not simple, but if done right, access, security, and privacy can co-exist to the benefit of all.
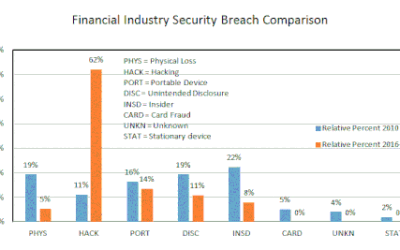
The Cost of a Data Breach
At some point in time, your business will be breached. There are numerous ways for your system to be breached, but the key is being prepared. If you have all your data segregated and encrypted appropriately, then this will help lessen the damage done by the data breach. If you have also gone through different scenarios that could happen – whether it be malware or threat – and have a response plan in place, this can assist in decreasing the cost of a data breach.
Hospital Security: Medical Devices and Bluetooth
Various studies and research have been done revolving around the lack of security for some medical devices. One of the main problems found lay with embedded web services that allow devices to communicate with one another and feed digital data directly to patient medical records.